Meterpreter allows hackers to access the target's system by running an invisible shell. It is used to establish a communication channel on the target machine. Meterpreter is famous among pen testers because of its power and versatility. Due to these qualities, the bad actors are attracted to them. Meterpreter contains all the basic features which are contained in the penetration testing tool. The features include profiling the network, running executables, access to the command shell, and sending and receiving files. These are not the only features of interpreters, they can do many more things. A few of its capabilities are post-forwarding, taking screenshots, privilege escalation, and keylogging. Using the in-memory DDL injection, the interpreter is deployed. Meterpreter creates no new processes, writes nothing to disk, and it resides entirely in memory. Instead, it injects itself into compromised processes from which it can migrate from one to other running processes as necessary. The forensic footprint of the attack is very less as a result. Due to these features, it becomes an attractive payload for APIs that prioritize staying under the radar. There are several ways to load the interpreter into memory. The Metasploit framework contains numerous stagers like document macros, VBScript, and Powershell. If we want to inject an interpreter directly into memory, this Metasploit framework also provides a large number of exploits. The loader and exploits can also write by advanced users, and they can use those loaders and exploits with their custom evasion techniques.
Meterpreter and Metasploit are constantly evolving. It was recently common that if we want to drop the stages of meterpreter on the disk and evade sandboxes and bypass the static scanners use as many packers as possible. For that, Metasploit has various easy-to-use and built-in encoders. To detect them, AV companies do struggle. Using the number of fileless techniques, interpreters, and Metasploit have been updated. For example, after exploitation and leveraging WinAPI, we will inject the payload into a system process to query the registry. In Metasploit, every time, more features are added. It provides a long list of auxiliary modules to list here as well as a fuzzer to find out the potential security flaws in binaries.
To circumvent the disadvantage of a specific payload, Meterpreter was designed to ensure encrypted communication and enable the writing of commands. When we use the specific payload, and the target system starts a new process, at that time, alarms may be triggered. This shows the drawback of using specific payloads. Meterpreter was originally written by Skape for Metasploit 2. x. Matt Miller uses the hacker moniker. For 3. x, the common extension was merged and is currently undergoing an overhaul for Metasploit 3.3. It is an advanced multi-function payload. When we don't have our tool, and we are standing in a remote system, Meterpreter helps us to leverage the capabilities dynamically at run time. Using the Meterpreter, we can easily exploit the systems which are in the exploited system's network but not in our network. An interactive shell is provided by Meterpreter, which helps us to use extensible features at run time. Due to this, the chances of successful penetration testing are increased.
Meterpreter Goals
- Meterpreter creates no new processes and writes nothing to disk because it resides entirely in memory.
- Meterpreter can easily migrate from one to another running processes as necessary. It injects itself into a compromised process.
- Encrypted communication is used by Meterpreter by default.
- At the time of the forensic report, the interpreter provides very little evidence as a result on the target machine.
Working of Meterpreter
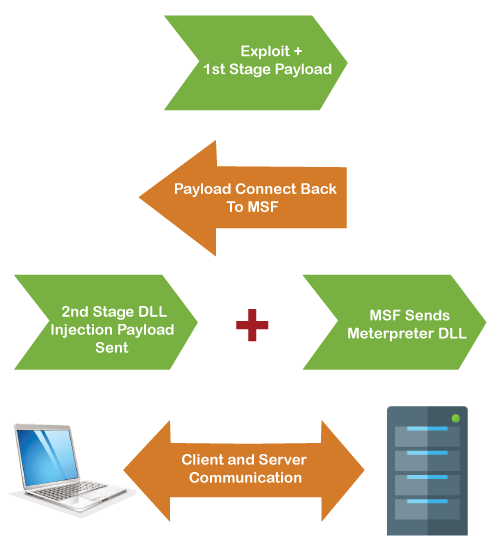
The hacker sends the first-stage payload to the target computer when a system is compromised. Meterpreter is connected back by this payload. Then it sends a second DLL injection, which is followed by the DLL of the meterpreter server. Using the interpreter session, client-server communication and a socket are established. It is encrypted, and this is the best part of this session. Due to this, confidentiality is provided. Hence, any network administrator may not sniff a session.
No comments:
Post a Comment