There are two types of traditional methods of information gathering:
- Passive information gathering
- Active information gathering
Passive Information Gathering
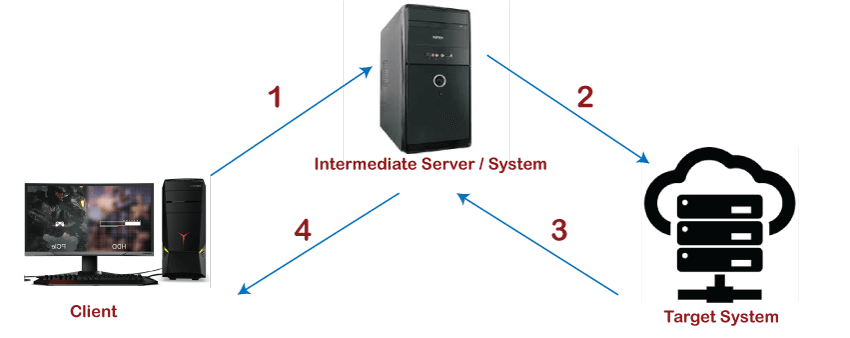
Before the active information gathering, passive information gathering will occur during the information-gathering phase. The purpose of passive information gathering is to collect information about the target network without establishing direct interaction with the target. It uses the intermediate system for interaction. In the information gathering, a blueprint of the target network infrastructure is prepared. Each and every branch has a unique blueprint. Passive information gathering does not directly interact with the target; that's why it is harmless for the target organization. Active information gathering is more aggressive as compared to passive information gathering. Passive information gathering does not require direct interaction with the target organization as compared to vibrant information gathering. In passive information gathering, the client probes the target system for information using the intermediate system. The description of passive information gathering is as follows where the client probes by the target system using the intermediate system:
In passive information gathering, when we perform information gathering, we have four intentions. These are as follows:
- We want to gather all the available information on the network about the target and about the target actively or passively.
- We want to find the versions of web servers, platforms, operating systems, etc.
- We want to perform techniques like DNS fingerprinting, Whois lookup, and other queries related to network and organization.
- We want to identify vulnerabilities and exploits so that we can launch the attack.
Passive information gathering gets the information of the target that is publicly available using the various passive methods:
Finance
We can either use yahoo finance or Google Finance to know the target's financial posture. It will help us to show whether the organization is losing shares or making money. Using the following link, we can find that:
https://www.google.com/finance
Alerts
If we are receiving updates on a particular subject using SMS or mail, it is generally provided by the Alert. To collect competitive information, this service is used. If we are a pentester, the alert can be used to monitor how the updates of clients Id fooled using the internet. We can use the following link to do this:
https://policies.yahoo.com/us/en/yahoo/privacy/products/alerts/
https://www.google.co.in/alerts
Archive
All versions of every website can be stored by archive.org using the internet. The archive is good for us if the target is updating its website, and we want to know the frequency of the updation. It can also be used to find the look of the previous version of the website. We can use the following link to do this:
Using Email, we can generate a discussion with the front desk or support. The address of the sender and receiver is contained in the email header, which is used to track geo-location. It also has the authentication method used, mail server's IP address, etc. Using the service point of mail; we can track our sent mail like its destination, path, when the mail was opened by the other person, etc. We can use the following link to track the mail:
http://whatismyipaddress.com/trace-email#
Whois Lookup
The information about the users that own registered domains is contained in the Whois database. The information about the owner of the website can be retrieved using the Whois database. The personal information about the owners of the site like the server's IP address, physical address, email address, phone number, registration date of site, expiry date of site, etc. Using the following link, we can do this:
https://centralops.net/co/DomainDossier.aspx?dom_whois=1
DNS Footprinting
Using DNS footprinting, the pentester can know more information about the target. The DNS information is extracted by the pentester from the DNS server. The information can have a mail server, domain name, IP address, computer names, etc. most commonly used domain names are as follows:
- Text record (TXT)
- Host information record (HINFO)
- IP Version 6 Address records (AAAA)
- Reverse-lookup Pointer records (PTR)
- Mail exchange records (HINFO)
- Start of Authority Record (SOA)
- Integrated Services Digital Network records (ISDN)
- Address Mapping Records (A)
- Name Server Records (NS)
- Canonical Name Records (CNAME)
Google Dorks
The search engine is the first method. The spiders or crawlers will take all the sensitive information of the target like credentials, URL, etc. if search engine crawlers are allowed by robots.txt of a site. We will craft special search queries to get this information from the spider or crawlers. We will use the following link to get the information:
inurl:certifiedhacker.com
We will copy the above query and paste it into Google. The query's answer will be all the URLs with certified hackers in them. This type of query is known as Google dorks, and this type of method is called Google hacking. In the Google hacking database of exploit db, we can see many useful queries.
https://www.exploit-db.com/google-hacking-database/
Active Information Gathering
Active information gathering is collecting more information about the target network by directly interacting with the target. It is illegal to do this without authentication. Active information gathering can use OS fingerprinting, port scanning, DNS enumeration, etc. The main goal of vibrant information gathering is to collect all the possible information about the target, just like passive information gathering. As compared to passive information gathering, active information gathering may reveal much more information. In vibrant information gathering, there are always chances that security alarms of the target system are going off. Since the target system and the attacker have a direct connection. All the requested information would be logged and can later be traced back to the source. In active information gathering, we can conduct a port scan to find out all the open ports on the target. We can also conduct scans to find out all the services that are running on the target network. Another opportunity for exploitation is given by the running services of each system. While performing active information gathering, if we become careless, we might be caught by the IPS (intrusion detection system) or IDS (intrusion detection system).
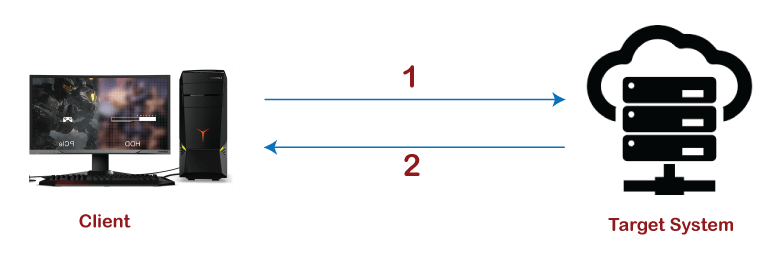
The description of active information gathering is as follows, where the target is directly probed by the client.

/how-routers-work-816456-final-5b2d68a6eb97de00369a4914.jpg)